Blog
We found and fixed critical security vulnerabilities in OpenClaw
How a deep codebase scan found 4 exploitable flaws
Victor Mier
Feb 5, 2026
OpenClaw is the open-source AI agent that's been all over tech Twitter. It lets you control your computer with natural language: read files, send emails, browse the web, run terminal commands. It went from zero to 145,000 GitHub stars in a few weeks.
It runs with full system access. It's also moving fast. Peter Steinberger made 6,600 commits in January, much of it AI-generated. That kind of velocity is impressive, but it makes thorough security review really hard.
We ran a codebase scan on it using cubic. Our agents found critical, exploitable vulnerabilities. We built fixes for the 4 most severe and submitted PRs. The OpenClaw team merged all of them within hours.
Here's what we found, why it matters, and how we fixed it.
How We Found Them
On February 2, 2026, we ran a cubic codebase scan on the OpenClaw repo. Thousands of AI agents analyzed the codebase in parallel, tracing data flows across files and checking for exploitable vulnerabilities.
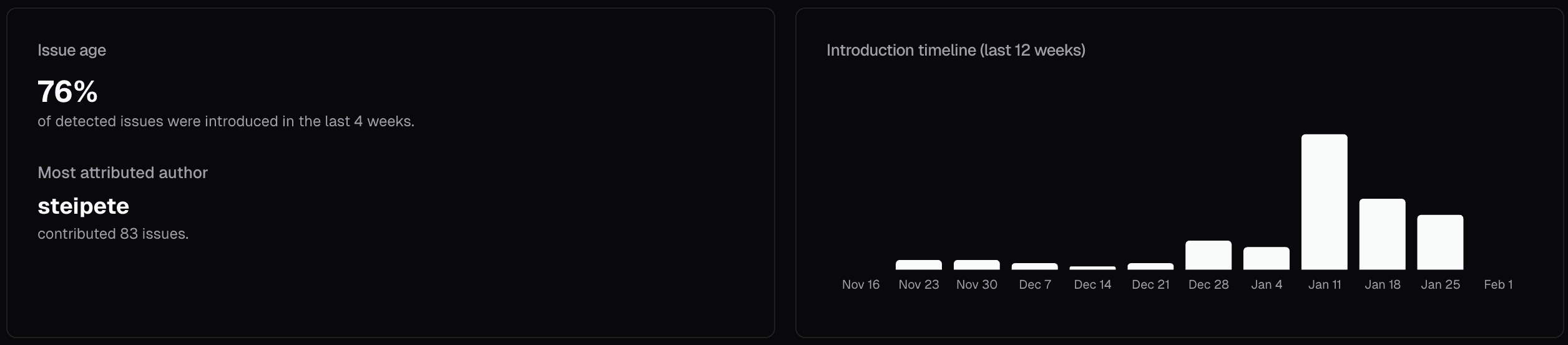
We evaluated each finding against OpenClaw's threat model. OpenClaw intentionally runs with significant system access, and users accept that tradeoff. But several of these vulnerabilities violated even that permissive boundary. These weren't configuration mistakes. They were core security flaws in correctly configured installations.
We prioritized the 4 with the highest real-world impact, built fixes, and submitted pull requests.
The 4 Vulnerabilities We Fixed
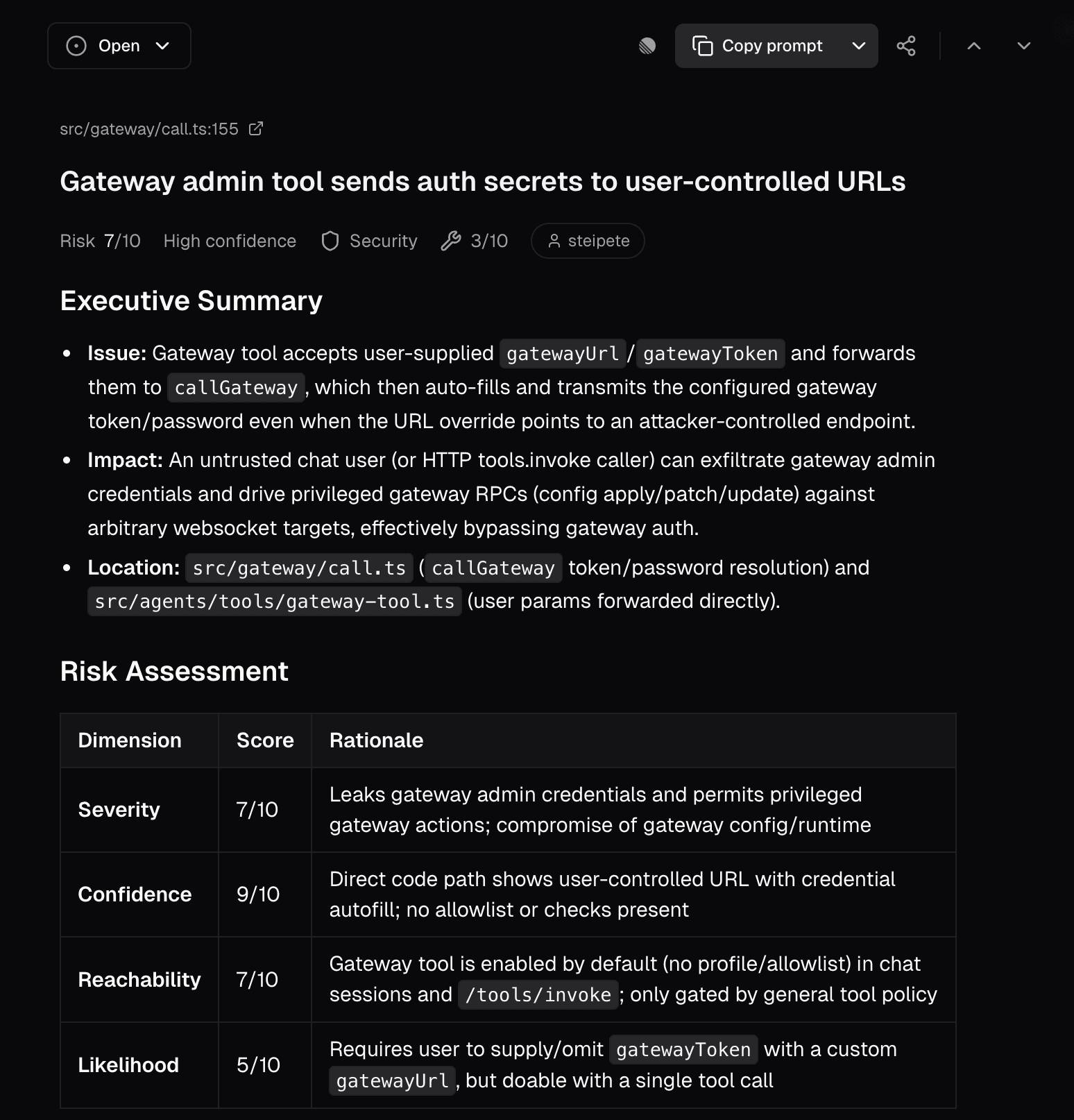
1. Gateway Credential Exfiltration via URL Override
A chat message can steal your gateway admin credentials. That's the short version.
OpenClaw's gateway is the central server that manages your AI agent. It handles tool execution, conversation history, and connections to services like WhatsApp and voice. Your gateway credentials give full control over your entire OpenClaw installation.
The gateway client automatically attaches locally configured admin credentials (from environment variables or config files) when connecting to a gateway URL. The problem: when the gatewayUrl parameter is overridden via tool arguments, the client still falls back to those local credentials. A chat message or prompt injection can point the client to wss://attacker.example/ws and receive real gateway tokens.
With stolen gateway credentials, an attacker gets full control over the OpenClaw installation: tool execution, conversation history, and all connected services.
A similar issue in the Control UI was patched as CVE-2026-25253 in January. Our scan found the same class of vulnerability in a different code path: the gateway client's tool interface.
The fix: When a URL override is provided, require explicit credentials. Don't fall back to local config.
PRs: Original #8113 | Merged #9179
2. OpenClaw Instance Hijack via WhatsApp Login
Any contact on your WhatsApp allowlist can take full control of your OpenClaw instance. Even if they fail, your gateway goes down.
OpenClaw lets you add contacts to an allowlist so they can message your bot through WhatsApp. The whatsapp_login tool generates a WhatsApp Web pairing QR code. This sensitive tool was available to all allowed senders, not just the owner.
When whatsapp_login is triggered while the gateway is running, creates a second WhatsApp connection using the same credentials. WhatsApp detects the conflict and immediately disconnects the existing session. The attacker scans theit new QR code and takes control of OpenClaw's WhatsApp channel.
The original owner doesn't just lose access. Their OpenClaw instance is actively hijacked. And even if the attacker fails to scan the QR in time, simply triggering the tool causes a denial-of-service by disconnecting the gateway.
The fix: Gate whatsapp_login to owner-only access. We added an explicit owner allowlist for sensitive operations and threaded senderIsOwner through the agent pipeline.
PRs: Original #8768 | Merged #9202
3. Voice Allowlist Bypass
Block your caller ID and you bypass the voice allowlist entirely.
OpenClaw's voice call feature includes an allowlist to restrict who can call your bot. A logic bug made this control completely ineffective.
The code used suffix matching instead of exact matching and didn't handle anonymous callers correctly. When a caller blocks their ID, Twilio returns "anonymous". Stripping non-digits yields an empty string. Since every string ends with an empty string, endsWith("") is always true. Anyone could bypass the voice allowlist by simply blocking their caller ID.
The fix: Reject calls with missing caller ID and use exact matching.
PRs: Original #8104 | Merged #9188
4. Sandbox Bypass via Media Parameter
Even with sandboxing enabled, an attacker can read any file on your system through the media parameter.
OpenClaw has a sandboxing feature that restricts file access to a specific directory. The message tool validates path and filePath parameters against the sandbox root. But it didn't validate the media parameter. A user could read arbitrary files by passing a file:// URL through media, bypassing the sandbox entirely.
The fix: Apply the same sandbox validation to the media parameter, with appropriate handling for HTTP URLs (allowed), data URLs (disallowed for media), file:// URLs (validated), and local paths (validated).
PRs: Original #8780 | Merged #9182
Why This Matters
None of these bugs are obvious. The voice allowlist bypass is a good example: suffix-matching logic that handles every normal input correctly but breaks on one edge case (anonymous callers). You could read that code in a PR review and approve it without a second thought.
That's the challenge with AI-generated code at this velocity. The volume of new code outpaces what any team can manually review. These bugs shipped in a project with 145,000 stars and thousands of contributors watching.
Our agents found them in hours because it could trace data flows and edge cases across the entire codebase in parallel. That's not a replacement for human review. It's a way to keep up.
Want to Find What's Hiding in Your Codebase?
Most of these weren't classic security bugs. They were business logic errors: a suffix match that should have been exact, a parameter that got skipped in validation, a credential fallback that was too permissive. The kind of bugs that look reasonable in isolation but break down at the edges.
cubic codebase scans find these. Not just security vulnerabilities, but logic bugs, missed edge cases, and broken assumptions across your entire codebase.
Book a demo to run one on your repository.
Disclosure Timeline
February 2, 2026 - Ran codebase scan on OpenClaw repository
February 2, 2026 - Identified 4 critical security vulnerabilities
February 3, 2026 - Submitted pull requests with fixes for all vulnerabilities
February 4, 2026 12:34 PM UTC - Contacted Peter Steinberger (OpenClaw founder) with detailed vulnerability report
February 4, 2026 10:13 PM UTC - OpenClaw team acknowledged receipt and began review
February 4, 2026 23:59 UTC - PR #9179 (Gateway Credential Exfiltration) merged
February 5, 2026 00:11 UTC - PR #9182 (Sandbox Bypass) merged
February 5, 2026 00:23 UTC - PR #9188 (Voice Allowlist Bypass) merged
February 5, 2026 00:49 UTC - PR #9202 (WhatsApp Hijack) merged
February 5, 2026 - Public disclosure after verification of fixes
All fixes referenced in this post have been merged into the OpenClaw main repository. Thanks to the OpenClaw maintainers for their responsiveness in reviewing and merging these security improvements.

